How To Set Up A GKE Private K8S Cluster - Part 2
In the second part of this blog, we see how we can expose the service running in private cluster with security settings.

By Rohit Sehgal
In Part-1 of this blog, we saw how can one deploy K8s with GKE in private settings for security reasons. Read more here:

In this blog, let’s delve into how one can expose the service running in private clusters with NEG, and make those NEG is accessible with IAP.
But first, what’s NEG and IAP?
- NEG stands for Network Endpoint Group, and represents a group of backends served by a load balancer (LB). This load balancer can be Ingress resource or Cloud-native LB. NEG basically point to the service, in GCP environment this is backend service wrapper around k8s service resource.
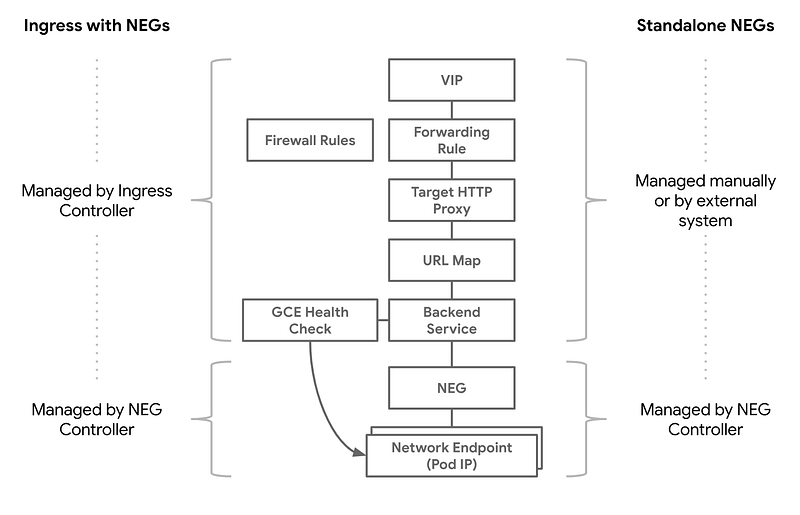
2. IAP stands for Identity Aware Proxy, and it provides a single point of control for managing user access to web applications and cloud resources running on GCP. You don’t have to configure anything of top of your application to integrate this with your application. If you are using Cloud-native LB, enabling IAP for services hosted with LB is a task that’s only a click away.

There could be various ways of exposing service from private clusters to public internet, but NEG is the most simple WRT to GCP. As GCP provides NEG resources, what you need to do is just add an annotation to service resource in K8s, like this:
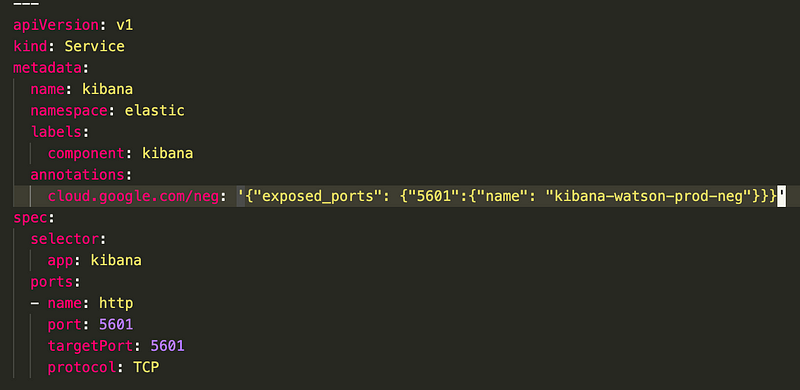
Since the NEG definition is tricky, make sure you expose service port through NEG as this will used in creating health check. So the port in NEG is port under ports not the targetPort.
Once the NEG is created, here are the next steps to be followed:
- Create cloud-native LB
- Create backend service to point to your NEG
- Create HC for backend service
- LB the frontend configuration as you like
- Securing access to service with IAP (optional)
While creating backend service select network endpoint group as we have created a service with that configuration.
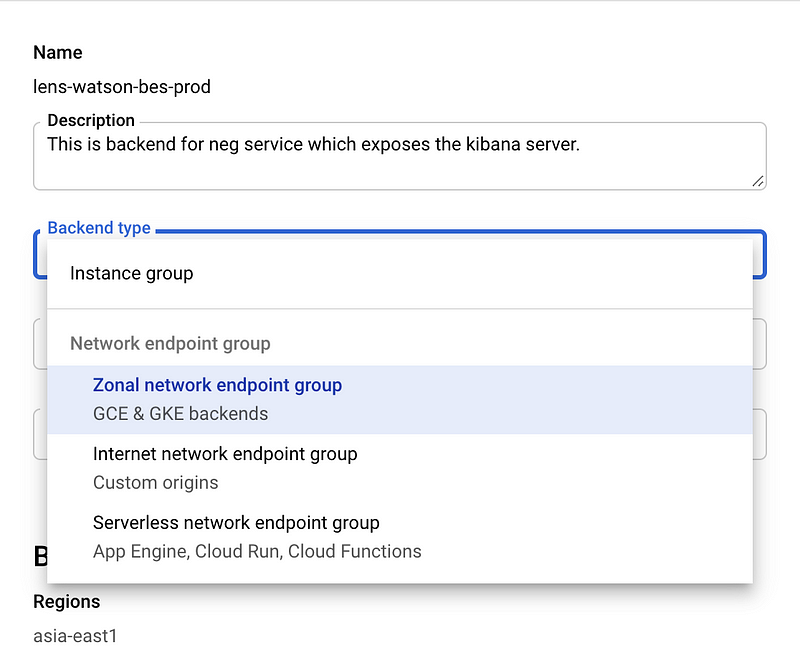
Pick the NEG from the drop down list. If your NEG creation was successful, the name should be appearing in the drop-down.

Create health check on serving port, or on fixed port 5601[NEG port].
Change frontend specs according to your configuration. Once you deploy LB with these changes, the service will be exposed to internet with configuration that you mentioned in the frontend configuration.
If you want to restrict access to only your organisation’s users to this service, go to the IAP page and select the backend service for which you want to enable IAP. This process is just a click away.
For the first time you may need to configure OAuth credentials for your project.
And using these steps, it gets increasingly easy to work on Private clusters, and exposing & securing services in Private clusters.

Find more stories from our vault, here.
Also, we’re hiring! Check out open job positions by clicking below:


